By Syed Jawad Imam Jafri, Cyber Security and Privacy Officer (CSPO), Huawei South Africa – 5G cyber security can be divided into three layers based on the security model in the communications industry: application security, network security, and product security (in descending order).
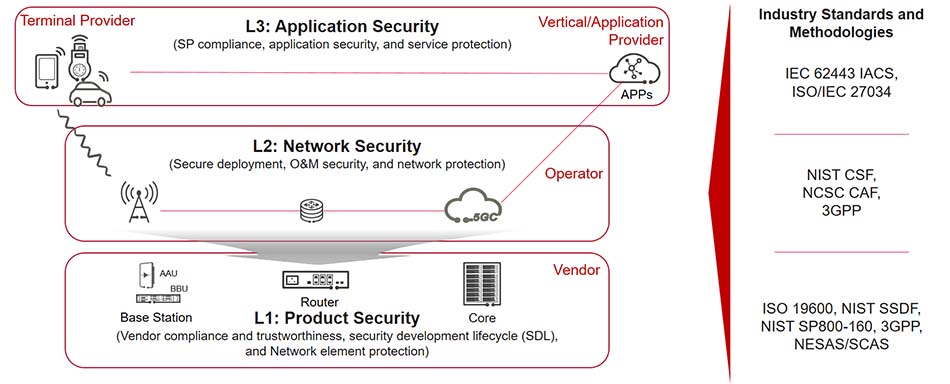
Figure 1: Three-layer cyber security model.
Application security is for both traditional mobile end users and vertical industries that provide or use a range of applications. This security layer requires collaboration among operators; device suppliers, and application providers to ensure the security of 5G networks and the users and services they support.
Application security is not heavily dependent on the security of network pipes. Vertical industries must take responsibility for the security of their solutions, protect critical assets at the application layer from network attacks, promptly detect security threats, and quickly restore basic services. The Open Web Application Security Project (OWASP) provides an excellent set of best practices on the development assurance for application security, including the application security threat analysis methodology, Application Security Verification Standard (ASVS), and penetration test guide. In addition, ISO 27034 provides systematic suggestions for ensuring application security from an organizational perspective, including identifying risks from three dimensions, defining application security levels, and establishing application security controls (ASCs) along with mapping organization normative framework (ONF).
Network security is usually managed and operated by operators. They consider network compliance and the security of network design, deployment, O&M, and operations, and continuously perform comprehensive risk assessment based on network components as well as the network equipment and architectures provided by vendors to ensure effective management of security threats. There are mature specifications and methodologies in the industry for reference. For example, the Identify, Protect, Detect, Respond and Recover (IPDRR) methodology defined by the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) can help operators systematically address cyber risks. The 3GPP also defines technical security specifications for network interworking.
Product security must be provided by equipment vendors. It focuses on the compliance, secure development process, and security capabilities of products. Security assessment is critical for product security. It provides a basis for assessing whether network equipment and components are designed and implemented in compliance with security requirements. NESAS, established by the GSMA and 3GPP together with global operators, equipment vendors, and third parties, is a widely recognized NE security assurance standard in the industry.
5G cyber security is a shared responsibility of key stakeholders, including operators, interconnection providers, equipment vendors, application providers, standards organizations, governments, and regulators, each with their own clearly defined responsibilities. These responsibilities, when fulfilled, can enable the secure deployment and operations of 5G systems.
